In our previous post, we introduced how we built AI-powered trading agents that can autonomously manage onchain portfolios while operating within strict security boundaries. Today, we'll dive deep into the technical architecture, examining the specific components and implementation details that make this possible.
The Foundation: GLAM's Access Control System
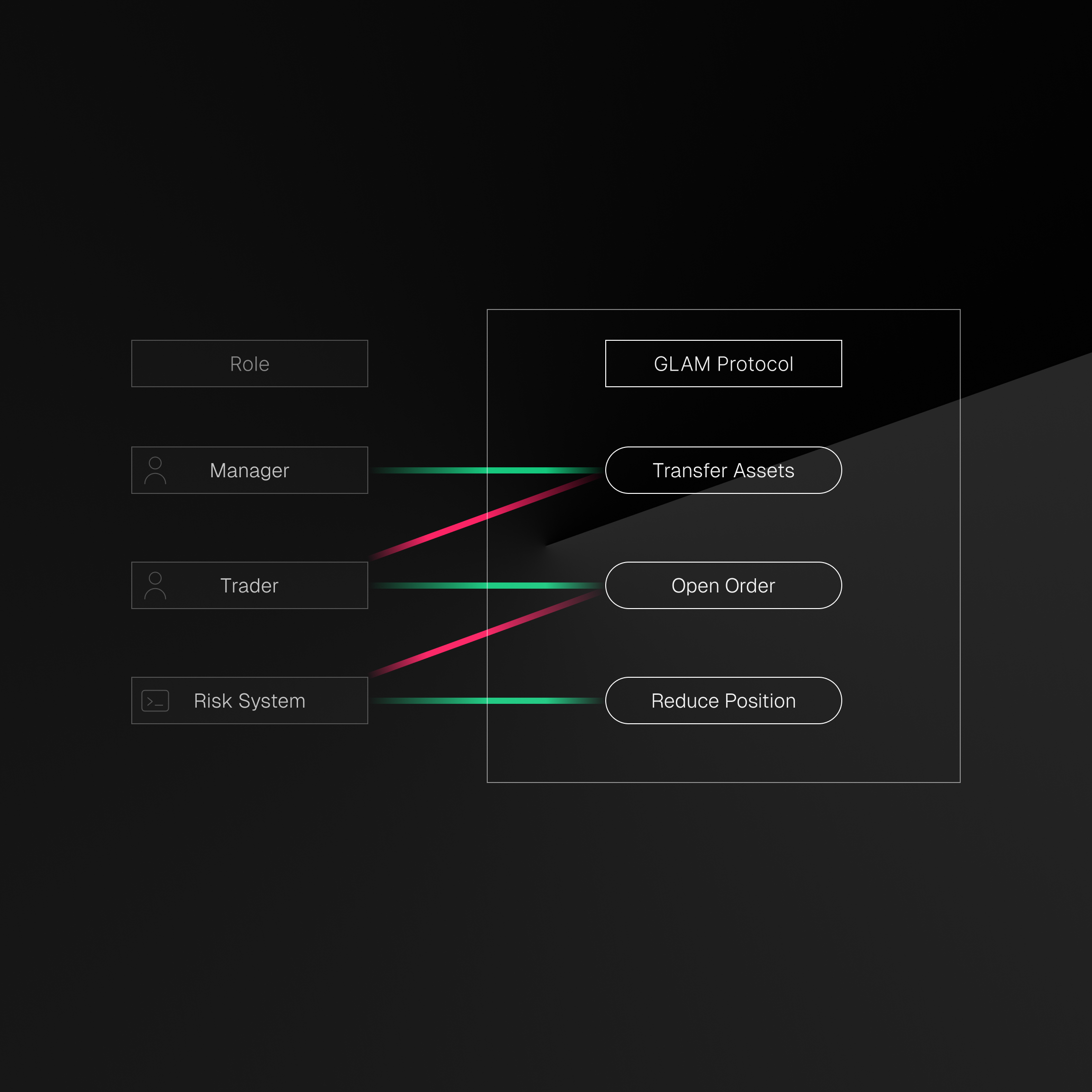
At the core of our implementation is GLAM's fine-grained access control system, which provides the security foundation for our AI agents. The protocol supports a comprehensive set of permissions that can be granularly assigned to delegates:
pub enum Permission {
DriftInitialize,
DriftUpdateUser,
DriftDeleteUser,
DriftDeposit,
DriftWithdraw,
DriftPlaceOrders,
DriftCancelOrders,
DriftPerpMarket,
DriftSpotMarket,
Stake, // Stake with marinade or spl/sanctum stake pool programs
Unstake,
LiquidUnstake,
JupiterSwapFundAssets,
JupiterSwapAnyAsset,
WSolWrap,
WSolUnwrap,
}This permission system is crucial for secure AI agent implementation as it allows us to:
- Precisely define what actions an agent can perform
- Protect treasury assets by limiting the scope of potential operations
- Implement a defense-in-depth approach to security
Technical Architecture
Our implementation consists of two key components working in tandem:
1. Fund Manager Agent
- Primary role: Strategy execution and decision making
- Implemented using AutoGen framework
- Has access to GLAM CLI commands
- Operates with restricted permissions (JupiterSwapFundAssets only)
2. Code Executor Agent
- Primary role: Command execution and output handling
- Runs in a Docker container with GLAM CLI pre-installed
- Handles direct interaction with the blockchain
- Reports execution results back to the manager agent
Implementation Details
Setting Up the Environment
First, we configure our agents using AutoGen's framework:
from autogen import ConversableAgent
from autogen.coding import DockerCommandLineCodeExecutor
from pathlib import Path
# Configure the execution environment
work_dir = Path("coding")
work_dir.mkdir(exist_ok=True)
executor = DockerCommandLineCodeExecutor(
work_dir=work_dir,
image="glam-cli",
stop_container=False,
timeout=120
)
# Initialize the code executor agent
code_executor_agent = ConversableAgent(
name="code_executor_agent",
llm_config=False,
code_execution_config={"executor": executor},
human_input_mode="NEVER"
)Fund Manager Agent Configuration
The fund manager agent requires specific knowledge about the environment and available commands:
fund_manager_system_message = """
You're a crypto fund manager that manages an index fund on the Solana blockchain that tracks 50% USDC and 50% WSOL.
Token addresses:
- WSOL: So11111111111111111111111111111111111111112
- USDC: EPjFWdd5AufqSSqeM2qN1xzybapC8G4wEGGkZwyTDt1v
Available commands:
1. env
2. fund balances
3. fund swap [-s <slippageBps>] [-m <maxAccounts>] [-d] <from_mint> <to_mint> <amount>
"""
fund_manager_agent = ConversableAgent(
"fund_manager",
system_message=fund_manager_system_message,
llm_config={"config_list": [{"model": "gpt-4", "api_key": os.environ["OPENAI_API_KEY"]}]},
code_execution_config=False,
max_consecutive_auto_reply=2,
human_input_mode="NEVER"
)Security Implementation
Permission Management
For our demo, we generated a keypair for the fund manager agent and restricted its permissions to only JupiterSwapFundAssets:
pubkey: "GLamA1CaNfV9XLuL6Z6GaXVifyu7dR2bCTxnoNwtNDQd"
permissions: [
{
JupiterSwapFundAssets: { }
}
]This ensures the agent can only:
- Query fund balances
- Execute swaps through Jupiter Protocol
- Trade only pre-approved assets
Automated Portfolio Management in Action
Let's examine a complete execution cycle:
- Balance Check
node /mnt/workspace/dist/cli/main.js fund balancesOutput shows:
Token Amount Value (USD)
SOL 0 0
So1...2 0.20013924 32.015126363277743- Trade Calculation The manager agent processes the balance information and determines:
- Current portfolio: 100% WSOL ($32.02)
- Target: 50% WSOL, 50% USDC ($16.01 each)
- Required action: Swap 0.1 WSOL to USDC
- Trade Execution
node /mnt/workspace/dist/cli/main.js fund swap -s 50 -d -m 20 So11111111111111111111111111111111111111112 EPjFWd5AufqSSqeM2qN1xzybapC8G4wEGGkZwyTDt1v 0.1The execution parameters ensure:
- 50 bps maximum slippage (-s 50)
- Direct routes only (-d)
- Maximum 20 accounts in transaction (-m 20)
Advanced Capabilities and Future Directions
This implementation demonstrates the foundation for more sophisticated trading strategies:
- Multi-Asset Portfolio Management
- Extend the permission system to handle multiple assets
- Implement complex rebalancing algorithms
- Add support for custom portfolio weights
- Risk Management
- Implement position size limits
- Add slippage protection
- Develop circuit breakers for unusual market conditions
- Strategy Optimization
- Incorporate market data feeds
- Implement dynamic rebalancing thresholds
- Add support for custom trading signals
Technical Considerations for Production
When deploying similar systems in production, consider:
- Error Handling
- Implement robust error recovery
- Add transaction retry logic
- Monitor for failed transactions
- Performance Optimization
- Cache frequently accessed data
- Optimize RPC calls
- Implement batch processing for multiple trades
- Monitoring and Logging
- Track all agent actions
- Monitor performance metrics
- Implement alerting for unusual behavior
Conclusion
This technical implementation demonstrates how we can combine AI agents with onchain security controls to create autonomous yet secure trading systems. The key innovation lies in the combination of:
- Fine-grained permission systems
- Secure execution boundaries
- Autonomous decision-making
As the ecosystem evolves, this foundation can be extended to support increasingly sophisticated trading strategies while maintaining robust security controls.
We're excited to see how the community builds upon these primitives to create the next generation of onchain trading systems. Reach out for early access to GLAM: hello@glam.systems

.png)

.png)
.png)